security email system unbmeta.online

Email security refers to the measures taken to protect email communications and information from unauthorized access, theft, or damage. As email has become an essential tool for communication and data exchange, it has also become a target for cyber-criminals. Protecting email information is crucial for individuals and organizations to maintain their privacy, confidentiality, and avoid potential loss of valuable information.
II. Proactive Email Security Measures
A. Strong Passwords
One of the simplest and most effective measures to protect email information is to have strong passwords. A strong password is one that is at least 8 characters long and includes a mix of letters, numbers, and symbols. It is also recommended to change passwords regularly and not use the same password for multiple accounts.
B. Password Rotations
Another proactive measure to ensure email security is to practice password rotations. This involves regularly changing passwords to reduce the risk of unauthorized access. Regular password rotations help to minimize the risk of password theft, as cyber-criminals often use stolen passwords to gain access to sensitive information.
C. Spam Filters
Spam filters are also an important proactive measure for security. They help to filter out unwanted and potentially harmful emails, such as phishing scams, from reaching the recipient’s inbox. Spam filters use various techniques, such as analyzing the sender’s reputation, subject line, and content, to determine if an email is spam.
D. Desktop-based Anti-Virus or Anti-Spam Applications
Desktop-based anti-virus or anti-spam applications can also be used to proactively protect email information. These applications are designed to scan incoming emails for malware or other security threats, such as viruses or spyware, and prevent them from reaching the recipient’s inbox.
III. Service Provider’s Email Security Measures
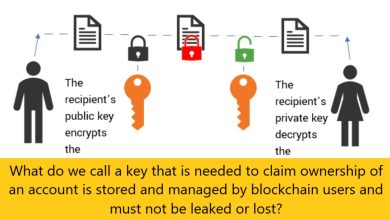
A. Encryption and Digital Signing
Service providers often offer encryption and digital signing to ensure security. Encryption involves converting email information into a code to prevent unauthorized access. Digital signing, on the other hand, involves adding a digital signature to an email to verify its authenticity and prevent tampering.
B. Firewall and Spam Filtering Applications
Service providers may also implement firewall and spam filtering applications to protect email information. Firewalls help to prevent unauthorized access to email servers, while spam filtering applications help to filter out unwanted emails. These measures are crucial for protecting email information and maintaining privacy.
IV. Importance of Email Security
A. Email is a Common Target for Cyber-Criminals
Email is a common target for cyber-criminals as it is an essential tool for communication and data exchange. Cyber-criminals often use various tactics, such as phishing scams or social engineering, to steal sensitive information. This highlights the importance of security measures to protect sensitive information and maintain privacy.
B. Loopholes in Email Security
Loopholes in security can also be exploited by cyber-criminals. For example, weak passwords or below-average standard security measures can easily be exploited, leaving email information vulnerable to unauthorized access.
C. Protection of Sensitive Information
Email security measures are crucial for protecting sensitive information, such as personal information or financial details. Security helps to prevent cyber-criminals from accessing sensitive information and potentially using it for malicious purposes.
D. Below-Average Standard Security Measures
Below-average standard security measures can also pose a threat to email security. For example, if a service provider uses weak passwords or outdated security measures, this can leave email information vulnerable to cyber-criminals.
E. Cyber-Criminals Use Sophisticated & Advanced Methods
Cyber-criminals are constantly developing new and sophisticated methods to target businesses and individuals. They use advanced techniques such as phishing scams, malware, ransomware, and social engineering to gain access to sensitive information and steal valuable data.
These methods are designed to be highly effective and difficult to detect, making it essential for businesses and individuals to stay vigilant and take proactive measures to protect themselves from cyber threats. This includes keeping software and security systems up-to-date, regularly backing up data, and being cautious when opening emails or links from unknown sources. Additionally, it’s important to educate employees and individuals about the dangers of cyber-attacks and the importance of following best practices for online safety.
V. Threats to Email Security
Email security is an essential aspect of the digital world, and with the advancement in technology, the threats to email security have become more sophisticated and challenging. Some of the key threats to security are:
- A. Phishing: Phishing is a malicious attempt to trick an individual or organization into providing sensitive information such as login credentials, credit card numbers, and other confidential data. The attacker disguises as a reputable source, such as a bank or a well-known organization, and sends an email that appears to be genuine, but it is not. The recipient is then prompted to click on a link that takes them to a fake website that looks similar to the real one.
- B. Social Engineering: Social engineering is an attack that takes advantage of human emotions and psychological tactics to gain access to sensitive information. The attacker may use tactics such as impersonating someone known to the target, using urgency and fear to convince the target to act quickly, or creating a sense of urgency to prevent the target from thinking logically.
- C. Ransomware: Ransomware is a type of malicious software that infects the computer system and encrypts all the data, making it inaccessible to the owner. The attacker then demands a ransom in exchange for the decryption key. Ransomware is a significant threat to email security because it can spread rapidly through the email system, infecting multiple computers and causing widespread damage.
- D. Identity Theft: Identity theft occurs when an attacker gains access to personal information, such as name, address, Social Security number, and other confidential data. The attacker can use this information to steal money, open new bank accounts, or apply for loans in the victim’s name.
VI. Importance of Advanced Email Security Measures
As the threats to email security become more sophisticated and challenging, it is essential to implement advanced email security measures to protect sensitive information. Some of the benefits of advanced email security measures include:
A. Better Threat Detection: Advanced email security measures use advanced algorithms and machine learning techniques to detect and prevent potential threats, such as phishing, spam, and malware. This provides a higher level of protection compared to traditional email security measures.
B. Protection Against Cloud Vulnerabilities: With the increasing use of cloud services, it is essential to secure email data in the cloud. Advanced email security measures provide protection against cloud vulnerabilities, such as data breaches and unauthorized access.
VII. Method of Securing Email Data
One of the key methods of securing email data is encryption. Encryption involves converting plain text data into a coded message that can only be decrypted by someone with the correct key. This provides a higher level of security and ensures that sensitive information remains confidential.
VIII. Conclusion
In conclusion, email security is an essential aspect of the digital world and is critical for the protection of sensitive information. With the increasing sophistication of cyber-attacks, it is imperative to implement advanced email security measures to prevent potential threats and ensure the confidentiality of sensitive information. Both individuals and organizations must take email security seriously to protect themselves from the consequences of a security breach.
People also Read: top3 profession show management software for you amytrader